CherryBlossom CTF | write-up

Hello all, this is my first write-up at this page If you see anything not right or have any corrections I would be very happy getting some feedback, anyways let's start our write-up, Today we'll review a CTF challenge on TryHackme CherryBlossom. This challenge is rated hard and it focuses on file manipulation and cryptography.
First of all, we will start enumerating the machine
nmap -sC -sV {target-host}

we can see that there are three open ports 22 for SSH and 139-445 used by Samba, so far we have nothing except the samba, let's move on and scan the smb
nmap --script smb-enum-shares -vv {target-host}

and here we have something, an Anonymous file shared which means we can dig in with anonymous account and we may find something interesting.
smbclient \\{target-host}\Anonymous
we found a text file journal.txt and when we open it, it contains a huge base64.
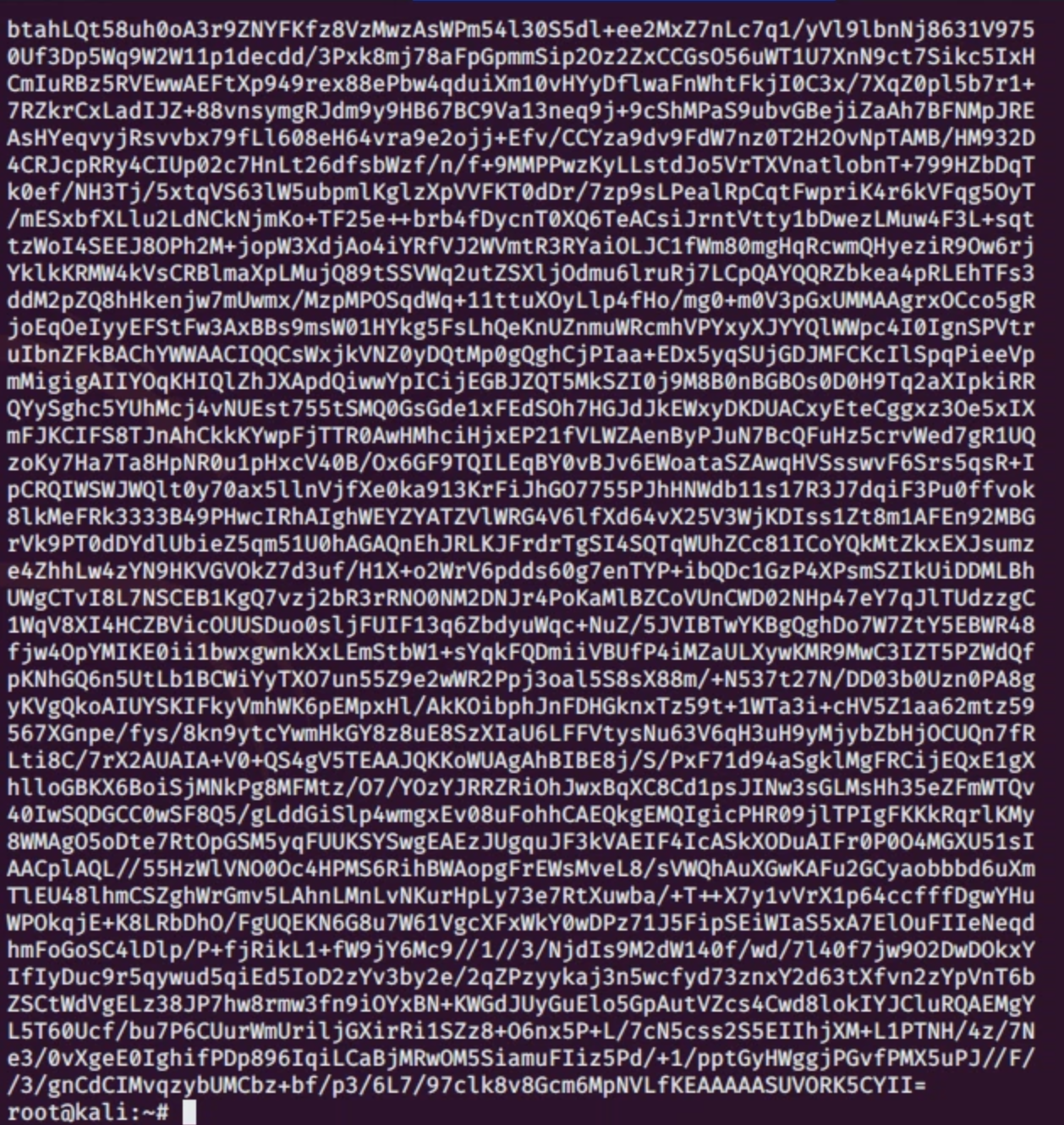


Decoding it provides us with an image, Let's save it as a png. After checking it with the command file, it is a PNG.

Normally, in Steganography challenges Jpeg are commonly used, Steghide won't be able to work on this PNG which means we will need to use another tool called stegpy, It's easy to install all you have to do is pip3 install stegpy and let's see what's hidden there
stegpy {file}


we got a zip file! Unluckily, it look like our file is corrupted, Let's check the hex of the file to see if something is wrong with the tag
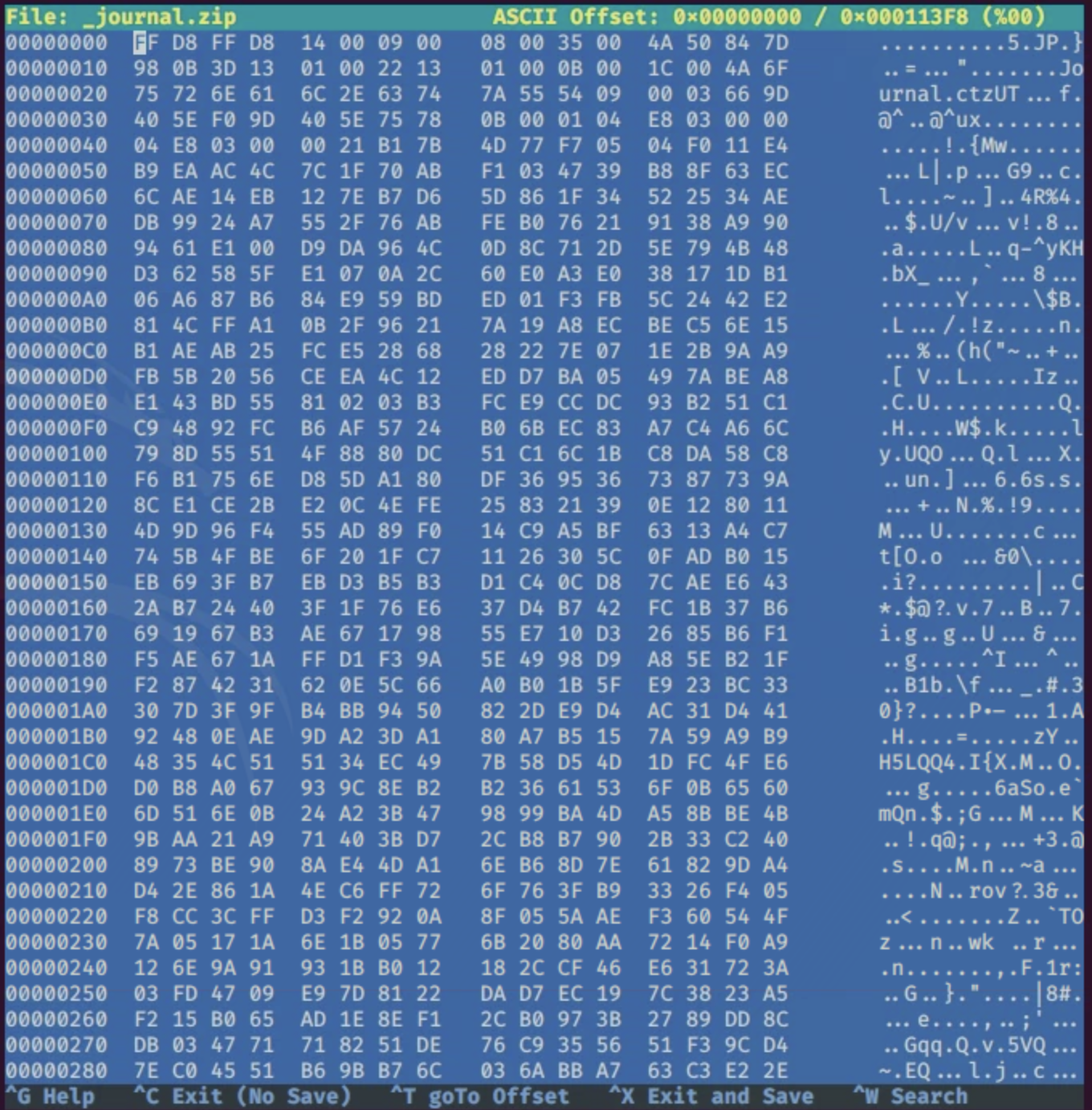
as it is provided in the picture it doesn't look fine, let's change it to what it's supposed to be 50 4B 03 04


exit and save, it works! if you have the password 😶, Let's move on and extract that hash from the file, I will use fcrackzip to decrypt it but feel free to use whatever you like.

after decrypting the zip file, found an Encrypted Cherrytree document, one of the good ways to store data and diaries ... , if we use the command file to check it, it will tell us that it's a 7z file, so let's 7z2john this baby file.


the diaries and privacy he had is shared with us, So let's have a look at what we've got there.

I exported the most interesting thing he had a wordlist called cherry-bolossm 🍒 and we got a username , this is getting fun now. Let's brute force the user lily password with the wordlist we exported from the file.


Welcome, Lily! 😊 what a fun way we got this user, let's not get lost now and focus on our box.
There's no user flag because there's another user that holds the flag and then the root! we got to pivot 😎 the username is Johan. Let's browse on this machine.

the shadow.bak can be read by us which means we have something to get us to Mr Johan.

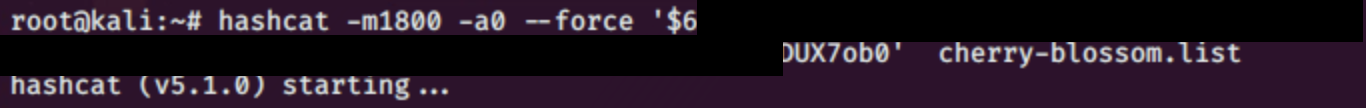

Et Voila, we decrypted the hash successfully and jumped from user lily to johan with the command:
sudo -u johan
we typed the password we got and we have the user flag, now what. We need to get root priv, the first thing I do when I'm trying to privesc sudo -l to see if the user is allowed to use anything as root and try to gain access with the power he got.
when I tried to type the password we got prompted to johan, which is weird and very unusual unsafe unwhatever, all I know is that we have a pwdfeedback (pasword feedback) issue which means we are using a vulnerable version of sudo, found out we have a (CVE-2019-18634) sudo buffer overflow

tried what I read about in that CVE and our sudo version burped a Segmentation fault, which means we have a bufferoverflow over here ...
talking about bufferoverflow if you don't understand the vulnerability here's a very good video linked


I downloaded the exploit coded in C language, gave it permission to be executed and boom we got a root user, all we have to do now is go to /root/ directory and the file root.txt fill contain our flag and here you go you are no longer upset with your low privileges.
I really enjoyed this machine, learned many things the diary thing encryption, cryptography 101, backups are bad with wrong permissions, and png can contain files, ... and mostly to not forget and make it clear for anyone who comes and ask me if the bufferoverflow ... YES, they do still exist!!
The bufferoverflow thing continues to be a feature of the security landscape as long as we are still using C language. This is in no small part due to the significant issue of legacy code. An awful lot of C code still exists, including the kernel of every major operating system and popular libraries such as OpenSSL. Even if the doctors, I mean the developers want to use a safe language such as C#, they may need to depend on a third-party library written in C.
Happy hacking!

